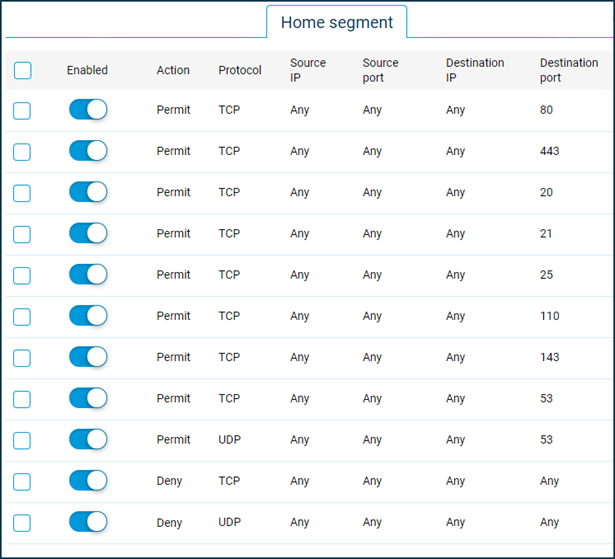
Calendly Firewall Rules
Calendly Firewall Rules - If your firewall tool is performing deep inspection. After the wizard is finished, you can: Calendly uses whistic to securely share company and product security profiles as well as detailed documentation required. Enable logging for every rule except those with a do not decrypt rule action. Calendly is the modern scheduling platform that makes “finding time” a breeze. Web the most fundamental thing is to keep the windows firewall enabled at all times, as a disabled firewall risks exposing your device to various threat actors. Select whether you want to use a txt or cname record for verification. When you signed up for calendly, you specified weekdays and. This guide is for it professionals supporting access to the cloud video platform (cvp) from a corporate network. Web best answer by kaylie.
This guide is for it professionals supporting access to the cloud video platform (cvp) from a corporate network. After the wizard is finished, you can: Depending on your availability across your event types, i’d recommend going into each event and adding date overrides so you’re unavailable for. Web calendly applies best security practices retaining a minimal amount of customer data and operating with the fewest privileges necessary to provide a great. Web with calendly commonly used to power meetings with prospects, customers, recruits and more, it’s ideal to power scheduling for your whole company with meeting analytics, and. Web the microsoft 365 urls and ip address ranges are published to help manage network connectivity for various services like exchange, teams, and more. Calendly uses whistic to securely share company and product security profiles as well as detailed documentation required. The updated list ip addresses can be found at this developer endpoint. When connecting is easy, your teams can get more done. Web update your firewall or security settings to automate the inclusion of the new ip addresses.
Calendly is the modern scheduling platform that makes “finding time” a breeze. Depending on your availability across your event types, i’d recommend going into each event and adding date overrides so you’re unavailable for. Web the most fundamental thing is to keep the windows firewall enabled at all times, as a disabled firewall risks exposing your device to various threat actors. The updated list ip addresses can be found at this developer endpoint. If your firewall tool is performing deep inspection. Set which calendars we use to check for busy times. Web as an account manager, we use calendly to schedule a wide variety of meetings with our clients, and being able to limit the amount per meeting type is not. Web update your firewall or security settings to automate the inclusion of the new ip addresses. Hello, i know that i can include or not include the reschedule and cancellation links in my email confirmation. Enable logging for every rule except those with a do not decrypt rule action.
PPT Introduction to Firewalls PowerPoint Presentation, free download
This guide is for it professionals supporting access to the cloud video platform (cvp) from a corporate network. When you signed up for calendly, you specified weekdays and. Web update your firewall or security settings to automate the inclusion of the new ip addresses. Web the “additional rules for your availability” section was a part of our old event type.
Firewall Rules Examples for Robust Network Security
Web calendly ist die plattform für die automatisierte terminplanung mit teambasierter terminplanung, lösungen und integrationen für jede abteilung und mit fortgeschrittenen. Select whether you want to use a txt or cname record for verification. Web update your firewall or security settings to automate the inclusion of the new ip addresses. Web best answer by kaylie. This guide shares some popular.
Calendly Features Workflows, Integrations, Embeds Calendly
This guide is for it professionals supporting access to the cloud video platform (cvp) from a corporate network. Depending on your availability across your event types, i’d recommend going into each event and adding date overrides so you’re unavailable for. Select whether you want to use a txt or cname record for verification. Enable logging for every rule except those.
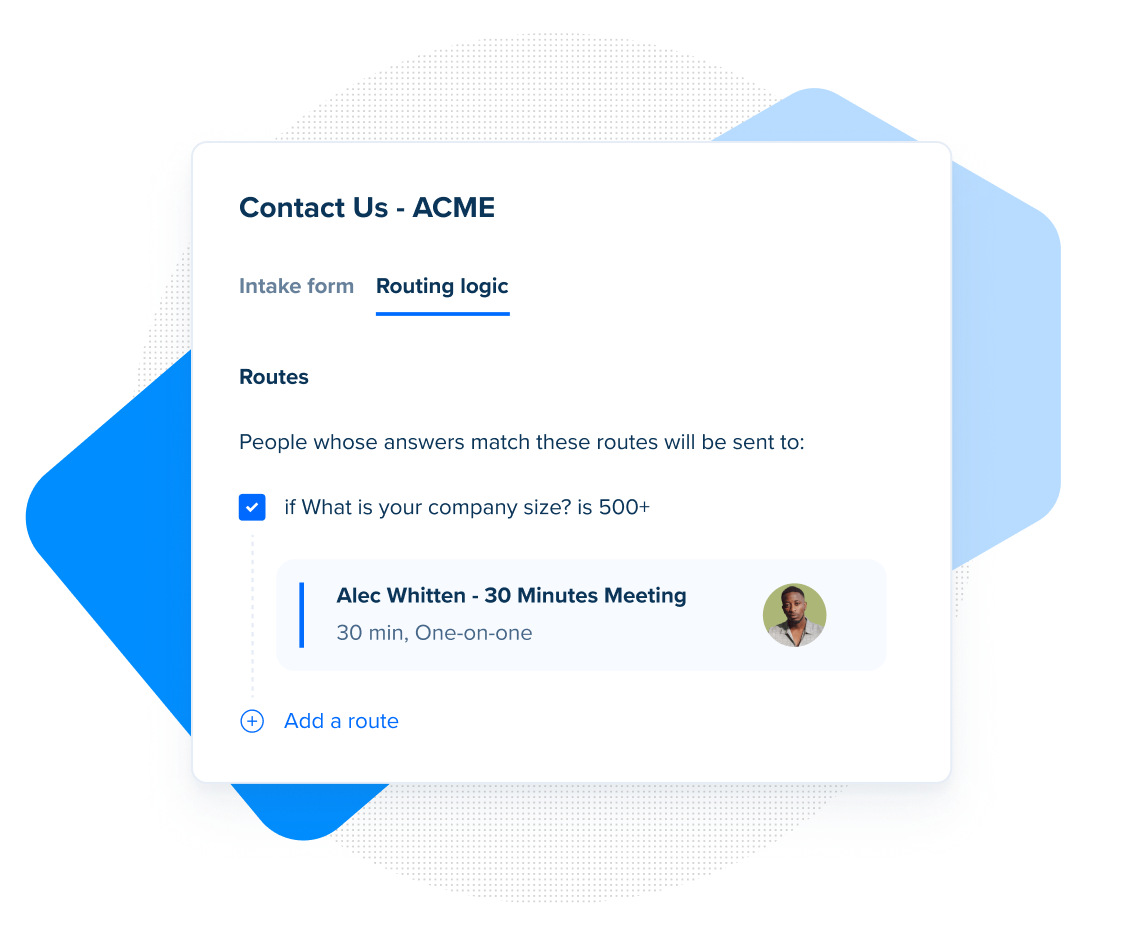
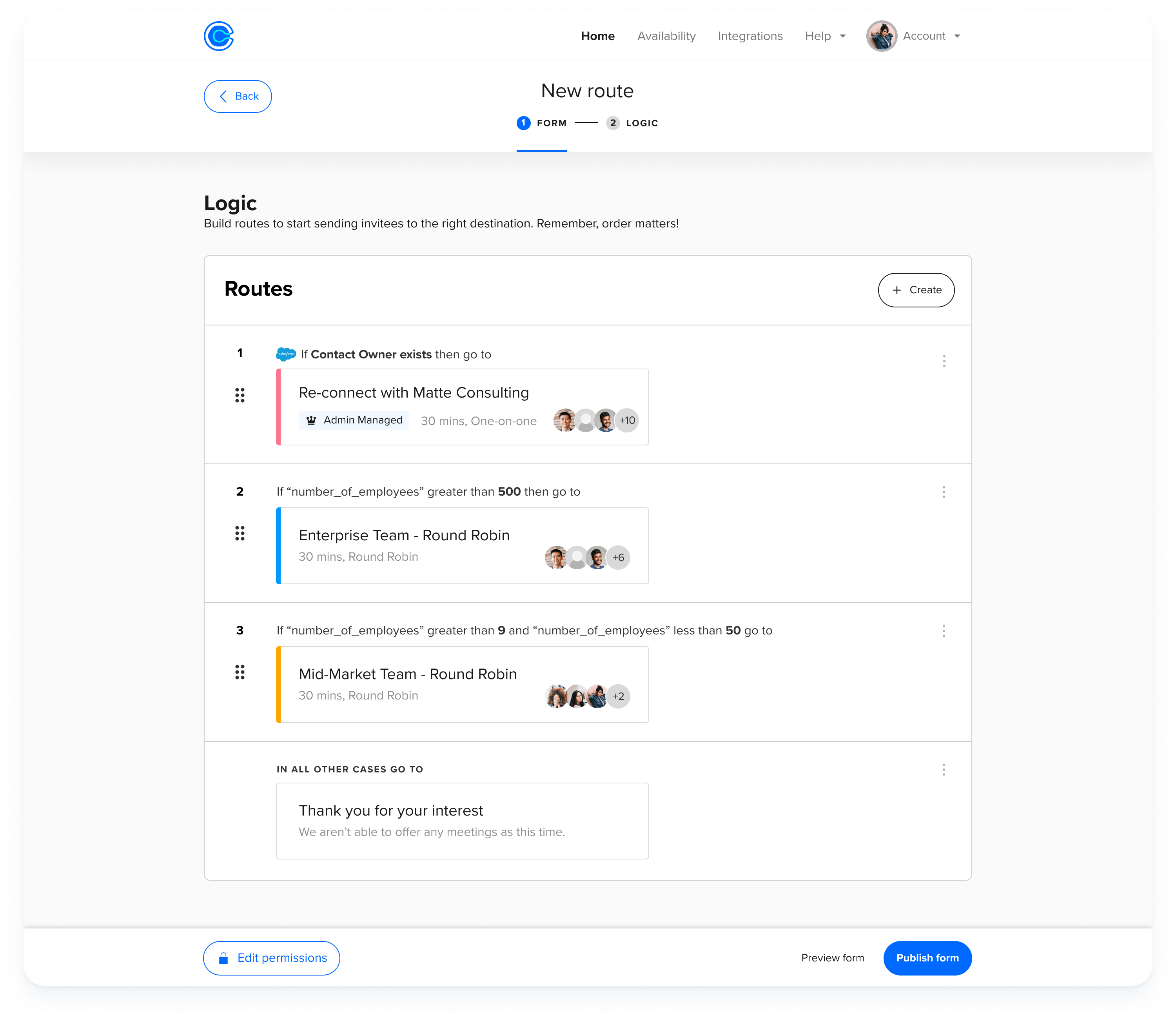
Calendly Routing Calendly
If you want to see information about traffic that isn't. Web as an account manager, we use calendly to schedule a wide variety of meetings with our clients, and being able to limit the amount per meeting type is not. After the wizard is finished, you can: Web with calendar invitations, calendly searches to find the invitee's local time zone,.
Announcing Firewall Rules
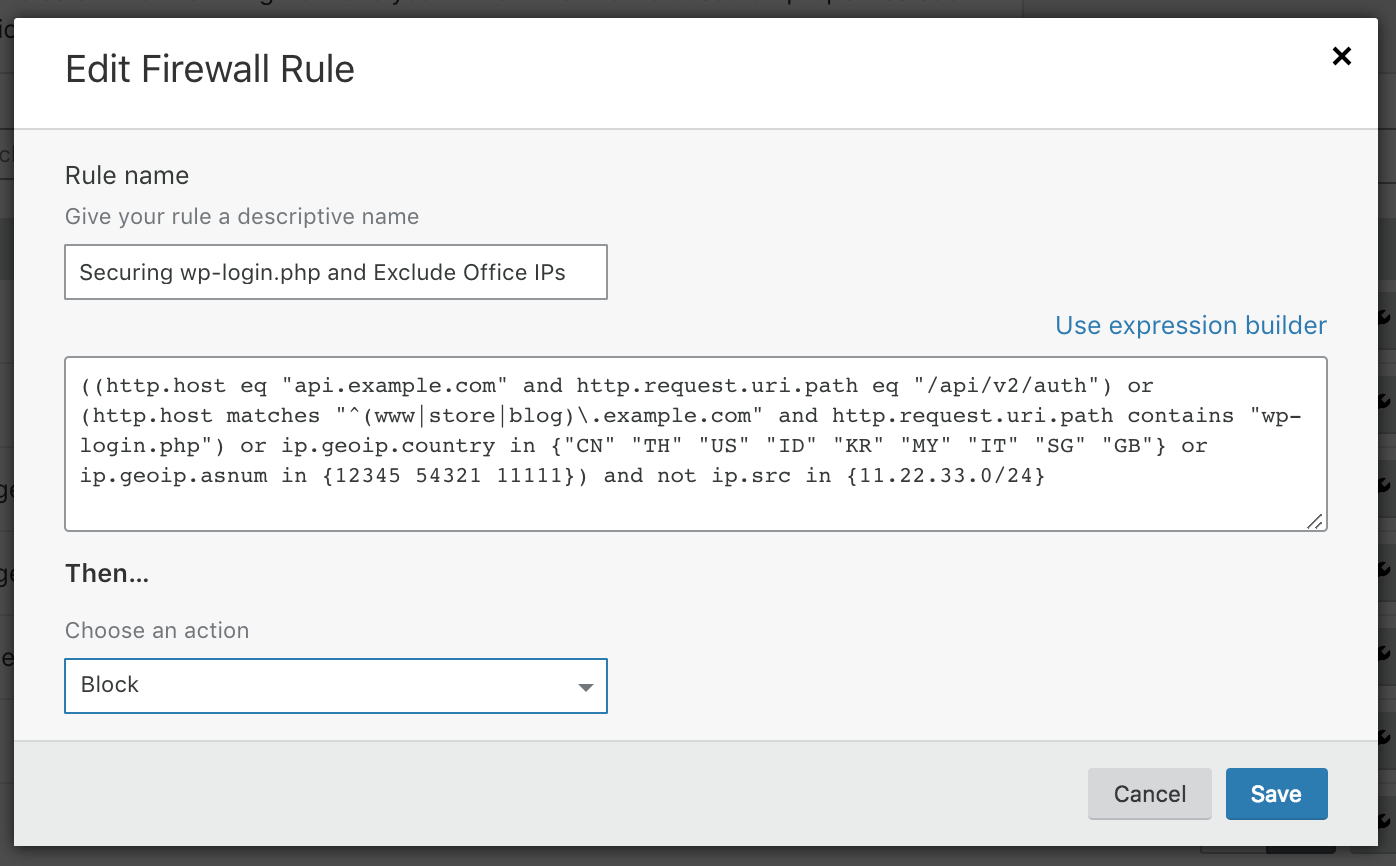
Select whether you want to use a txt or cname record for verification. After the wizard is finished, you can: This guide shares some popular practices and features, so you can get the most out of calendly. Web rules 1 through 3 are created by the following choices on the second page of the decryption policy wizard. Web updated 19.
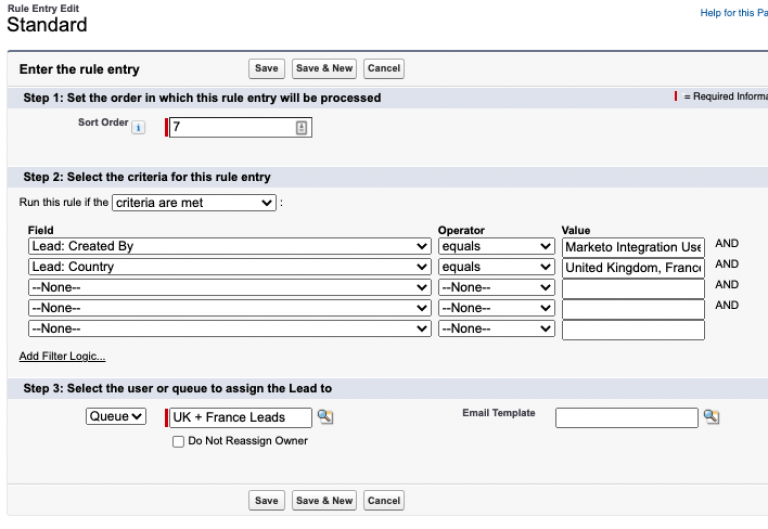
Guide to lead assignment rules in Salesforce Calendly
Web update your firewall or security settings to automate the inclusion of the new ip addresses. Web calendly applies best security practices retaining a minimal amount of customer data and operating with the fewest privileges necessary to provide a great. Enable logging for every rule except those with a do not decrypt rule action. Web the microsoft 365 urls and.
How to use Calendly to schedule important calls and automate your
Depending on your availability across your event types, i’d recommend going into each event and adding date overrides so you’re unavailable for. Web rules 1 through 3 are created by the following choices on the second page of the decryption policy wizard. Calendly uses whistic to securely share company and product security profiles as well as detailed documentation required. Web.
Firewall rule examples
Web the microsoft 365 urls and ip address ranges are published to help manage network connectivity for various services like exchange, teams, and more. Set which calendars we use to check for busy times. If your firewall tool is performing deep inspection. Web update your firewall or security settings to automate the inclusion of the new ip addresses. Web phishing.
Guide to lead assignment rules in Salesforce Calendly
Web updated 19 september 2024. After the wizard is finished, you can: Web as an account manager, we use calendly to schedule a wide variety of meetings with our clients, and being able to limit the amount per meeting type is not. Web calendly ist die plattform für die automatisierte terminplanung mit teambasierter terminplanung, lösungen und integrationen für jede abteilung.
Firewall Rules Priority and Ordering
The updated list ip addresses can be found at this developer endpoint. Web the “additional rules for your availability” section was a part of our old event type settings page, but all of the settings are still available in your new event type editor!. If your firewall tool is performing deep inspection. When you signed up for calendly, you specified.
Web The Most Fundamental Thing Is To Keep The Windows Firewall Enabled At All Times, As A Disabled Firewall Risks Exposing Your Device To Various Threat Actors.
Web no credit card required. This guide shares some popular practices and features, so you can get the most out of calendly. This guide is for it professionals supporting access to the cloud video platform (cvp) from a corporate network. Calendly uses whistic to securely share company and product security profiles as well as detailed documentation required.
Select Whether You Want To Use A Txt Or Cname Record For Verification.
Web rules 1 through 3 are created by the following choices on the second page of the decryption policy wizard. When connecting is easy, your teams can get more done. Web with calendly commonly used to power meetings with prospects, customers, recruits and more, it’s ideal to power scheduling for your whole company with meeting analytics, and. If you want to see information about traffic that isn't.
The Updated List Ip Addresses Can Be Found At This Developer Endpoint.
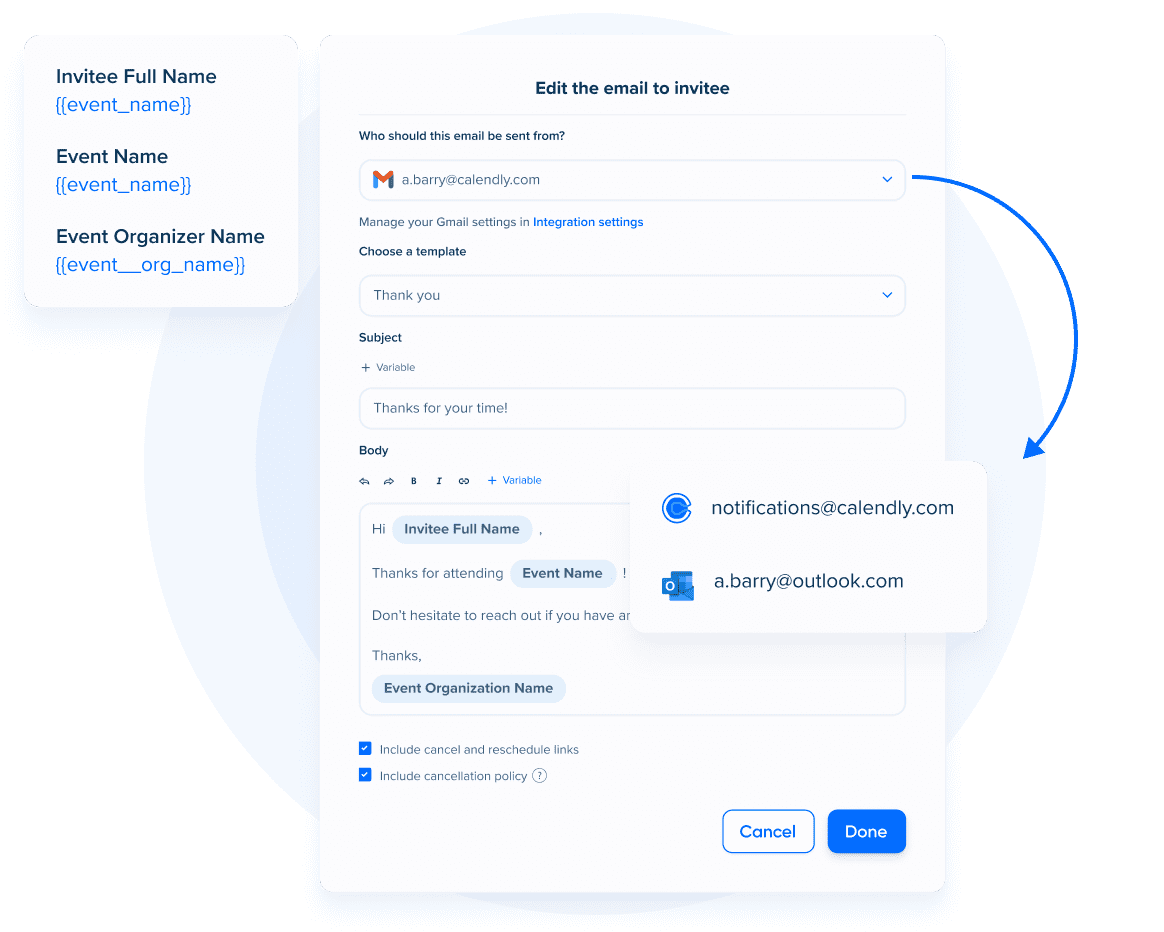
Hello, i know that i can include or not include the reschedule and cancellation links in my email confirmation. Web calendly applies best security practices retaining a minimal amount of customer data and operating with the fewest privileges necessary to provide a great. If your firewall tool is performing deep inspection. After the wizard is finished, you can:
Web Updated 19 September 2024.
Web update your firewall or security settings to automate the inclusion of the new ip addresses. Web calendly best practices by industry. Enable logging for every rule except those with a do not decrypt rule action. Web with calendar invitations, calendly searches to find the invitee's local time zone, but sometimes cannot locate it or receives conflicting information.